Welcome to CFInfluencia, a distinguished series by CyberFrat, where we celebrate the unsung heroes of cybersecurity. Join us on a journey of recognition and appreciation as we showcase the remarkable stories and professional journeys of cybersecurity professionals. Through this exclusive series, we aim to shine a spotlight on their invaluable contributions, passion, and dedication in safeguarding the digital realm.
In this edition, we are thrilled to have Ronita Sengupta, a trailblazer in technology and a powerhouse in the HR domain, sharing her inspiring journey.
Please Note: The views expressed are those of the author/interviewee.
I embarked on my journey in the IT Industry in 2013 with a passion for employee well-being and helping them manage change. As an HR and communication professional, I recognized the pivotal role effective communication plays in incident response. Early in my career, I actively sought opportunities to bridge the gap between technical experts and non-technical stakeholders.
My commitment to fostering a collaborative environment led me to engage in various forums, where I gained insights into the industry’s intricacies. I immersed myself in learning about emerging threats, compliance standards, and best practices, translating this knowledge into communication strategies and organizational practices that resonate with diverse audiences.
Over the years, I have cultivated an understanding of the unique challenges within the cybersecurity landscape through my interaction with industry experts and working in the IT space. I have worked in close coordination with information security and compliance teams, facilitating streamlined communication during high-stakes situations.
My journey has been marked by a commitment to continuous learning. I actively pursue training and stay in sync with industry trends to enhance my proficiency in navigating the dynamic IT landscape. Through workshops, webinars, and networking events, I have built a robust professional network, fostering collaborations that contribute to the collective knowledge base.
In summary, my trajectory in the IT Industry has been shaped by a fusion of HR expertise, communication acumen, and a genuine dedication to employee upliftment. I am poised to bring these multifaceted skills to the organization, contributing to its mission of fostering resilient and informed employees.
Besides being acknowledged as an impactful HR and communications professional, I have been recognised by Fox Story India as one of the top 100 women influencers in our country. I have been featured in Her story Inspiration and the Indian History of Women’s Museum. In 2019, I won the first runner-up title in the Mrs. India International Pageant and was an English News anchor with Delhi Doordarshan for more than 10 years.
To emerging leaders in the cybersecurity industry, my foremost advice is to recognize the symbiotic relationship between effective leadership and a resilient cybersecurity environment. In my 19+ years of journey in the industry I’ve witnessed the transformative impact leadership can have on any organization’s cybersecurity culture.
Firstly, prioritize fostering a culture of security awareness and inclusivity. In a field where collaboration is crucial, leaders should champion an environment where employees feel empowered to report potential threats without fear of retribution. Open communication channels and regular cybersecurity training sessions can significantly contribute to creating a vigilant workforce.
Secondly, embrace a proactive stance in addressing the human element of cybersecurity. Recognize that employees are not merely end-users but integral components of the organization’s defence mechanism. Provide continuous awareness on the latest cyber threats and equip the team with the knowledge to identify and respond effectively. Additionally, cultivating a sense of responsibility among employees towards the organization’s cyber resilience is essential.
In the realm of change management, I advise new leaders to approach cybersecurity as an ongoing evolution rather than a static set of protocols. Stay agile and adaptable, fostering a mindset that is responsive to emerging threats and industry advancements. Encourage a culture of continuous learning, enabling your team to evolve alongside the rapidly changing cybersecurity landscape.
Lastly, lead by example in championing a holistic approach to cybersecurity. Acknowledge that it is not solely the responsibility of the IT and Cybersecurity department but a collective effort that involves every individual in the organization.
In conclusion, my advice to new leaders in the cybersecurity industry is to embody leadership that prioritizes people, fosters a culture of continuous learning, and recognizes the collective responsibility for cybersecurity.
In the dynamic landscape of the cybersecurity industry, two prominent threats that demand attention are phishing attacks and insider threats. As an HR professional and communication professional, I recognize the critical role of proactive communication in mitigating these risks.
To tackle phishing attacks, fostering a culture of cyber awareness among employees is paramount. Regular training programs, simulated phishing exercises, and clear communication about the evolving tactics of cybercriminals can fortify the human firewall.
Addressing insider threats involves a comprehensive approach that extends beyond technological solutions. Emphasizing a positive work culture, encouraging open communication channels, and conducting periodic reviews contribute to early detection. Sensitizing leaders to the importance of their role in cybersecurity and involving them in fostering a cyber-resilient culture can significantly enhance the organization’s overall defence posture.
As a newcomer to CyberFrat, I am immensely grateful for the opportunity to engage in a fireside chat on the crucial topic of “Navigating the Digital Storm: Corporate Communication Strategies in Cyber Incident Response.” Being invited as a panelist is an honor, and I am eager to contribute insights, especially from the perspective of an HR professional, to the conversation. I express my sincere gratitude to CyberFrat for this opportunity.
I am a Dynamic Technology Audit, Risk, and Control professional with a rich 13+ years of experience in BFSI industry audits for various lines of business, such as investment banking, wholesale payments, cloud, and data privacy. My mission is to add value to each client by providing independent and objective assurance and advisory services on their IT and business control environment.
People: the weakest link in cybersecurity With a matured training and awareness program framework, we can safeguard this link and make systems and processes more secure.
Endeavour to give your best consistently in whatever you pursue on the professional and personal front I am greatly influenced by the Bhagwat Geeta: as it quotes, you are only entitled to the action, never to its fruits Continuous learning and upgrading oneself is very important to keep pace with rapid changes technology. On job learning we do during our day job. Off-job, you can learn via self-study, attending external training and conferences, and obtain professional credentials. Also, as part of giving back to community, you can conduct knowledge-sharing sessions, webinars, etc. Also, I believe that fitness is for everyone irrespective of gender, age, genetic lineage, or ethnicity. Taking care of one’s health is the best investment for anyone. To take care of others, one should be fit and fine by oneself. The more you sweat in peace, the less you bleed in war.
Consistency and discipline are two key traits needed for bodybuilding. It mirrors the same for professional careers too. Also, it helps me to keep grounded as we all are same on the gym floor: weights don’t treat you differently based on who you are, they give results to one who puts in efforts!
I am also a Brand Ambassador at Information Sharing and Analysis Center, a nonprofit organization that facilitates the exchange of cyber threat intelligence and best practices among its members. In this role, I leverage my expertise in Technology Audit, information security, cyber laws, and financial crime compliance to promote awareness and collaboration among the cyber community. I am passionate about staying updated and sharing my knowledge on the latest trends and developments in the Technology control and risk domain.

Information security is becoming more important than ever in our digital world. Organizations are looking for qualified people to safeguard their important data and assets as cyber threats continue to develop and become more sophisticated.
One of the most prestigious and widely recognized qualifications for information security professionals is the Certified Information Systems Security Professional (CISSP) certification. In this ultimate beginner’s guide, we’ll explore what CISSP is, its requirements, how to become certified, the CISSP exam, associated costs, training options, concentrations, benefits, statistics on information systems jobs, and CISSP salaries.
CISSP, short for Certified Information Systems Security Professional, is a certification offered by (ISC)², the International Information System Security Certification Consortium. CISSP is designed to validate the expertise and knowledge of information security professionals. It is widely regarded as a benchmark for professionals working in the field of cybersecurity. CISSP covers a broad spectrum of security topics, making it an excellent choice for those aspiring to become security experts.
Before you can pursue the CISSP certification, you must meet certain prerequisites. These requirements are designed to ensure that candidates have the necessary background and experience to tackle the CISSP exam effectively:
Becoming CISSP certified involves several steps:
Knowledge and skills in various information security domains. The eight domains covered in the exam are:
To pass the exam, you need to demonstrate your proficiency in each of these domains. Proper preparation is crucial, and many candidates opt for formal training or exam prep courses.
There are several training options available to help you prepare for the CISSP exam:
Earning the CISSP certification offers several advantages, including:
After completing CISSP certifications one can get many job roles in the security domain top ones include:
In addition to the standard CISSP certification, (ISC)² offers specialized concentrations for CISSP holders who want to deepen their expertise in specific areas of cybersecurity. As of my last knowledge update in September 2021, the available concentrations were:
Becoming a CISSP-certified professional can be a rewarding career move, providing you with the knowledge and credentials needed to excel in the dynamic field of information security. With the ever-increasing importance of cybersecurity, CISSP certification can open doors to a wide range of opportunities in both the public and private sectors. For more information and full CISSP training visit: learn.cyberfrat.com.

Can you imagine a walkie-talkie? A walkie-talkie that’s used for war emergencies?
A network is an important piece in the puzzle of technological development. It has a key function in communication between people and resources. Furthermore, it is a class of computers and devices that are so connected that they allow information to be exchanged between the parties involved.
Similarly, the Mobile Ad-Hoc Network is a temporary (ad-hoc) network of freely (mobile) moving nodes in a tech device that doesn’t need a centralized infrastructural network. The mobile network connects the nodes one by one, forming a chain of communication to send data packs and other useful information.

In this article, we will discuss MANET in terms of its
Basic Features
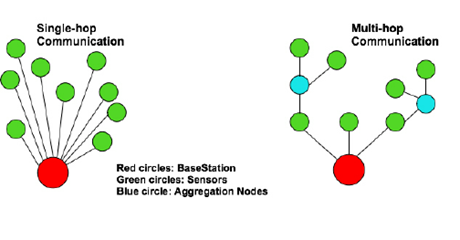
Multihop Routing
MANET system does have its useful applications but there are some challenges attached to it. MANET has a restricted wireless transmission range and a time-varying wireless link. Not much is transmitted as the network is mobile in nature. Such networks are also subject to obstruction and interference, affecting the data rate and consistency. Additionally, node movements can lead to errors and breakages. There are battery constraints that make the quality of service less satisfactory. Another challenge is security. It is one of the main challenges because data packets need to be transferred easily and safely to the other node.
Every system seeks one thing, and that is Security. As MANET is mainly fraught with security challenges, the solutions involve two approaches. One is proactive and the other is reactive. The proactive approach attempts to thwart threats through cryptographic techniques while the reactive approach seeks to detect threats and act accordingly. For example, most secure routing protocols adopt a proactive approach to secure routing messages while the reactive approach is used for protecting packet forwarding operations.
In the ideal scenario, both approaches should be applied as per the requirement. These approaches need to incorporate prevention, detection, and reaction.
When it comes to prevention, it is said that deterring the attacker has been infeasible when it comes to MANET as mobile devices are prone to compromise or physical sturdiness. Therefore, the detection and reaction component work for occasional intrusions.
In MANET, the prevention component is mainly achieved by secure ad-hoc routing protocols that prevent the attacker from installing incorrect routing states at other nodes.
Ad Hoc Protocols such as DSR (2), AODV (1), and Destination-Sequenced Distance Vector (DSDV), and employ different cryptographic primitives for example, HMAC, digital signatures, hash chains) are used to authenticate the routing messages.
The detection part identifies abnormal behaviour by malicious nodes. Such a thing is observed in an end-to-end manner or by neighboring nodes through overhearing.
Once the detection is identified, the reaction component sees adjustments in routing and forwarding operation, ranging from avoiding the node in route selection to collectively excluding the node from the network.
MANET is an emerging technology that has its benefits and at the same time challenges. Therefore, the applications of MANET are very useful whereas the security component can be tackled with some security mechanisms.
A stalwart in the segment of cybersecurity and info security, QRC Assurance and Solutions has become a trusted partner for clients globally. They have helped organizations to implement high standards of security and privacy practices within the organizations, enabling them to meet their data security and privacy compliance goals.
With humble beginning and transformation, the CEO of QRC Assurance and Solutions, Mr. Vamsi Krishna Maramganti, has bestowed people with his inspirational and practical ways of building risk-mitigation solutions for a storming world. This story of Cyber CEO is here to guide you and put light on Mr. Vamsi’s grit, determination & achievements and how the organization “QRC Assurance and Solutions” is simplifying various compliances to meet all business and regulatory requirements with their business-as-usual methods.
Mr. Vamsi is a tech enthusiast, problem solver, and nurturer. He advances with over 20+ years of rich experience in areas like Information Security, the Payment Card Industry, Quality Management, Data Privacy, Operational Risk, and Compliance management. He has worn different hats of an Information Security Auditor, Process Auditor, Quality Consultant, System architect, and Country Head of Operations within various organizations.
When founding QRC Assurance and Solutions, his primary objective was establishing a reliable and trustworthy cyber-infosec service. Through his company, he has played a significant role in offering comprehensive and regulatory-compliant solutions.
Although the company was established in 2016, the idea of building QRC Assurance and Solutions began taking up space when he started working after graduation, i.e., 20 years ago. With this zeal, he ascended toward his company, and his goals wherein, he strived for passionate cybersecurity aspirations that impacted countless lives.
In a span of 7 years, QRC Assurance and Solutions has expanded its horizons where it is:
As a transformer, Vamsi believes in P&P “Positive and Proactive” attitude is a must for having undefeated success. Additionally, he attains his inspiration from his team, customers, worthy competitors, and upcoming entrepreneurs.
Coming to his employees, he emphasizes the importance of an empathetic and compassionate approach. He recognizes that they are the backbone of the company and bears the responsibility to cultivate and retain their talents. While he encourages healthy competition among his team members, he also encourages them to surpass their personal best and achieve their full potential. He perceives his employees as more than just colleagues, but rather as valuable partners in the venture.
In addition to expanding his business ventures, Mr. Vamsi is known for his altruism and humanitarian acts. He firmly believes in the saying, “Charity Begins at Home,” and makes it a priority to give back to his community. His efforts involve ensuring that his employees have access to social security that extends to their families, as well as actively engaging them in various charitable endeavours. Mr. Vamsi says that his team finds ways to give back to society with a tint of discreet but impactful actions.
QRC Assurance and Solutions is a registered operation that started in the year 2016 under the initiative of Mr. Vamsi Krishna Maramganti. As a trusted partner, QRC covers every fine domain of enterprise data security and privacy services including data security audits, risk assessments, and privacy impact assessments to identify vulnerabilities and risks in an organization’s data management practices.
The team of certified professionals holding credentials like CISSP, CISA, PCI QSA, PCI SSF QSA, 3DS Assessor, OSCP, ISO/IEC 27001 LA, ISO/IEC 27701 LA, ISO/IEC 9001 LA, COBIT, CEH, CHFI, CCNA, PMP, etc, are dedicated to helping businesses achieve compliance with various data security and privacy regulations.
Within seven years of presence, QRC has established itself as a prominent player in the Payment Card Industry Certifications field by offering exceptional services and comprehensive solutions in Data Security and Privacy. QRC is not only a PCI QSA company but also an ISO certification body for ISO 27001 and ISO 27701, an established CPA firm, SWIFT Assessment Provider, and listed with CERT-In as Auditors, a unique set of qualifications achieved by only a handful of organizations. A hat on this list is QRC Assist, a Compliance and Project Management Tool of QRC for its customers. These credentials and Software coupled with the skilled & certified resources position QRC to assist any organization in achieving their data privacy and compliance goals.
Today, QRC Assurance and Solutions operations have successfully completed over:
With regards to QRC Assurance and Solutions, Mr. Vamsi has ambitious plans where he stands on the idea that there is a thin line between personal and professional life. Moreover, he intends to serve the clients, widen the client base, and judicially use the current resources. Constructing and growing the venture by being the determinative employer is one of the important keys for QRC Assurance and Solutions as a whole.
Automation has been around for many years, and it has come a long way in terms of its capabilities and applications. One of the latest trends in automation is Robotics Process Automation or RPA for short.
Robotic Process Automation (RPA) is an emerging technology that is revolutionizing the way businesses operate. RPA is a software tool that allows businesses to automate mundane and repetitive tasks, freeing up time for employees to focus on more complex and high-value tasks
Robotic Process Automation is a technology that uses software robots to automate business processes. RPA tools are designed to mimic human actions, such as logging into applications, copying and pasting data, and performing calculations. Software robots can perform these tasks much faster and more accurately than a human, which can lead to significant cost savings for businesses.
RPA is not a new technology, but recent advancements in artificial intelligence and machine learning have made it more powerful than ever before. RPA software can now learn from previous interactions and adapt to new situations, making it a highly effective tool for automating a wide range of business processes.
The benefits of RPA are numerous. Here are some of the most significant advantages:
RPA can be applied to a wide range of industries and business processes. Some of the most common applications include:
Robotic Process Automation is an emerging technology that is changing the way businesses operate. RPA can automate mundane and repetitive tasks, freeing up time for employees to focus on more complex and high-value tasks. The benefits of RPA include increased efficiency, cost savings, improved accuracy, increased scalability, and improved customer experience. With the ability to automate a wide range of business processes, RPA is quickly becoming a must-have technology for businesses that want to remain competitive in today’s fast-paced business environment.
The acquisition strengthens iValue’s capabilities in the Hybrid Multi-cloud Services area covering Managed Security services, Managed IT & Infra services, and Professional services for its OEMs and Channel Partners covering Compute, Network, Secure, Store, Virtualisation, and Database technologies.
iValue InfoSolutions, India’s premium technology solutions and services aggregator, today announced their acquisition of ASPL Info Services, a Bangalore-headquartered technology service enterprise revolutionizing businesses with best-in-class IT and Cyber security services for Hybrid Multi-cloud enterprise needs. ASPL Info drives success for global enterprises, mid-market businesses, and SMBs thru their network of partners across India, SAARC, MEA, and Southeast Asia geographies.
Established in the same year of iValue, in 2008, ASPL Info has worked extensively with 120+ Customers including leading enterprises cutting across sectors and geographies including India, the UAE, Nepal, Australia, Madagascar, Mauritius, and Gambia. The company addresses its customers’ unique and evolving business needs with a strong team of 150+ Infra & Security specialists, operating the 24*7 managed SOC and NOC and achieving an impressive 97+% SLA adherence year on year to deliver a comprehensive fleet of Managed IT Services, customized services, and enterprise tools transforming monitoring and security postures. Enterprises see ASPL Info as a long-term strategic partner they trust for high-quality results, one-of-a-kind packaged SERVICE offerings, crafted for their needs, and a consistent service experience. iValue’s Partner& OEM community can leverage this robust and extensive service capability to expand their offerings for their customer base.
“We are thrilled to welcome the ASPL Info team to the iValue family as it strengthens our SERVICES play across Managed Datacentre and Security services, and Professional Services. ASPL Info comes with matured project management processes, methodology for service delivery, strong SOC & NOC teams, modular service offerings, and strong customer success management.”
This presents us with a great opportunity to expand and build service offerings around iValue solutions, with the help of more tech alliances, geography expansion, and PS & MS business for our Partners and OEMs. This further augments iValue’s unique positioning in the market around the Services-led Solution Distribution focus.

I am confident that ASPL Info will deepen our engagement with OEMs & Partners in alignment with our core business thus expanding our addressable market.” said Shrikant Shitole, CEO, iValue Infosolutions.
“We are excited to join hands with a leader like iValue with an impressive track record of driving adoption of cutting-edge technology solutions across Cybersecurity, Datacentre, and Multi-cloud for the last 2 decades. iValue’s large eco-system of OEMs and Partners will accelerate ASPL Info’s growth and together we would meet and exceed our customers, OEMs, and Partners’ growth needs. This is much in sync with the ASPL Info Brand Purpose: To be a trustworthy team for our stakeholders empowering them at each step to achieve their business goals.”

In today’s increasingly hybrid and complex digital environment, we look forward to taking to iValue’s Partners and OEMs our distinct ability to build authentic relationships and deliver customer satisfaction with excellence.” said, Jayanth Gojer, CEO of ASPL Info Services.
Marketing contact:
Nagesh H Belur | [email protected] | +91 95359 99484
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Understanding the nuances of cyber insurance is paramount for businesses of all sizes. Far from being a mere buzzword, cyber insurance has emerged as a crucial component of a comprehensive risk management strategy. With the ever-evolving threat landscape and the potential financial ramifications of cyber-attacks, the importance of cyber insurance cannot be overstated.
Cyber insurance, also known as cyber liability insurance or cyber risk insurance, is designed to provide financial protection to businesses in the event of cyber incidents. These incidents may include data breaches, network damage, ransomware attacks, and other forms of cyber-attacks. Cyber insurance policies vary in coverage, but they typically encompass expenses related to forensic investigations, legal fees, notification costs, and public relations efforts to manage the aftermath of a cyber incident.
The proactive nature of cyber insurance is particularly noteworthy. It goes beyond financial protection by offering pre-emptive support in the form of risk assessments, employee training, and proactive security measures. By integrating cyber insurance into their risk management framework, businesses can bolster their cyber security posture and demonstrate their commitment to safeguarding sensitive data.
The escalating frequency and sophistication of cyber-attacks have underscored the critical need for cyber insurance. According to a study by the Ponemon Institute, the average cost of a data breach in 2020 was $3.86 million, showcasing the substantial financial impact of cyber incidents. Furthermore, the reputational damage and loss of customer trust following a breach can have long-term repercussions for businesses.
Amidst these challenges, cyber insurance serves as a crucial safety net, offering financial protection and support to navigate the legal and regulatory complexities associated with data breaches. It also helps businesses recover from the operational disruptions caused by cyber incidents, minimizing the potential long-term impact on their bottom line and reputation.
Recent trends in cyber insurance indicate a significant uptick in demand, with businesses across various industries recognizing the need to fortify their cyber security measures. According to a report by CyberPolicy, the global cyber insurance market is projected to reach $20 billion by 2025, reflecting a growing awareness of the financial and reputational risks posed by cyber threats.
Moreover, the evolving nature of cyber-attacks, including ransomware, phishing schemes, and supply chain vulnerabilities, has prompted insurers to offer more comprehensive cyber insurance policies. These policies are tailored to address the evolving threat landscape and provide businesses with the necessary coverage to mitigate the impact of cyber incidents.
When considering cyber insurance, businesses must conduct a thorough assessment of their unique cyber security risks and vulnerabilities. This entails evaluating the nature of their data assets, the regulatory environment in which they operate, and the potential financial impact of a cyber incident. By understanding their specific risk profile, businesses can align their cyber insurance needs with the level of coverage required to mitigate potential losses.
One key aspect of assessing cyber insurance needs is understanding the scope of coverage offered by different policies. This includes examining the extent of coverage for first-party and third-party losses, business interruption, extortion payments, and regulatory fines. Additionally, businesses should consider the value of pre-incident services offered by insurers, such as risk assessments, employee training, and incident response planning.
Selecting the right cyber insurance policy involves careful consideration of several key factors. Businesses should seek policies that align with their risk profile, industry-specific regulations, and the potential impact of cyber incidents on their operations. It is essential to engage with reputable insurance providers who have a proven track record in the cyber insurance space and can offer tailored solutions to address specific cyber risks.
Furthermore, businesses should pay attention to the breadth of coverage offered by a policy, ensuring that it encompasses a wide range of cyber incidents and associated expenses. This includes coverage for forensic investigations, legal and regulatory costs, notification expenses, credit monitoring for affected individuals, and public relations efforts to manage the fallout of a data breach.
A comprehensive cyber insurance policy should encompass a range of essential features to provide robust protection against cyber threats. These features may include coverage for data breach response expenses, cyber extortion payments, business interruption losses, and coverage for regulatory fines and penalties. Additionally, policies that offer pre-incident services such as risk assessments and employee training can help businesses proactively strengthen their cyber security posture.
Another critical aspect of a comprehensive cyber insurance policy is the inclusion of coverage for social engineering fraud, which addresses losses resulting from fraudulent schemes that manipulate individuals into transferring funds or providing sensitive information. Given the rising prevalence of social engineering attacks, this coverage can significantly mitigate the financial impact of such incidents on businesses.
In the event of a cyber incident, the claims process for cyber insurance plays a pivotal role in facilitating a swift and effective response. Businesses should familiarize themselves with the claims submission requirements and the documentation necessary to support their claim. This may include evidence of the cyber incident, financial records detailing the impact of the incident, and communication with law enforcement, if applicable.
Insurers typically have designated cyber incident response teams or external vendors to assist businesses in navigating the claims process. These teams can provide guidance on incident response best practices, forensic investigations, and legal compliance, ensuring that businesses can effectively leverage their cyber insurance coverage to mitigate the impact of the incident.
The landscape of cyber insurance providers is diverse, with numerous insurers offering a wide array of cyber insurance products. When evaluating potential providers, businesses should consider the insurer’s financial stability, claims handling reputation, and the breadth of coverage offered in their policies. It is also beneficial to engage with insurers who have a deep understanding of the evolving cyber threat landscape and can provide tailored solutions to address specific industry risks.
Moreover, some insurers offer value-added services in addition to traditional cyber insurance coverage. These services may include access to cyber security experts, incident response planning, and ongoing guidance on cyber risk management, thereby enhancing the overall value proposition of the cyber insurance policy.
The need for cyber insurance extends across businesses of all sizes, from small and medium enterprises to large corporations. While the scope of coverage and specific risk considerations may vary based on business size, the fundamental importance of cyber insurance remains consistent. Small businesses, in particular, are increasingly targeted by cyber criminals due to their perceived vulnerability, making cyber insurance a critical component of their risk management strategy.
For larger enterprises, cyber insurance serves as a vital tool to mitigate the substantial financial and reputational risks associated with cyber incidents. It provides a layer of financial protection to navigate the complex aftermath of data breaches and cyber-attacks, allowing businesses to focus on their recovery efforts without bearing the full brunt of the financial burden.
In conclusion, the imperative nature of cyber insurance in today’s digital landscape cannot be overstated. As businesses navigate the complex terrain of cyber threats and data breaches, cyber insurance stands as a crucial ally, providing financial protection, pre-emptive support, and a pathway to resilience in the face of cyber incidents. By understanding their cyber insurance needs, selecting the right policy, and leveraging the comprehensive features offered by insurers, businesses can fortify their cyber security measures and demonstrate their unwavering commitment to safeguarding their digital assets. In a world where cyber threats continue to evolve, the decision to secure cyber insurance is not only a strategic choice but a fundamental necessity for businesses seeking to fortify their defenses against digital perils.
This comprehensive blog article aims to provide insights into the significance of cyber insurance, the key considerations in choosing the right policy, and the evolving landscape of cyber insurance providers. By delving into the nuances of cyber insurance, businesses can equip themselves with the knowledge to make informed decisions and fortify their cyber security posture in an era where the digital landscape demands nothing less than unwavering resilience and proactive risk management.
By embracing the proactive protection offered by cyber insurance, businesses can not only mitigate the financial impact of cyber incidents but also instill trust and confidence in their stakeholders, showcasing their commitment to safeguarding sensitive data and fortifying their resilience against the ever-evolving threat landscape. As the digital frontier continues to evolve, cyber insurance stands as a cornerstone of robust risk management, enabling businesses to navigate the complexities of cyber threats with confidence and resilience.